We Calculate Your Human Risk
To better understand and manage the human element in your cyber security, we’ll take you through:
A scan of your company domain name
This will identify any potentially malicious or fraudulent domains that could be used in phishing campaigns of other cyber-attacks.
A scan of the dark web
This involves the monitoring the dark web for mentions or discussions related to your organisation's sensitive information.
A phishing simulation campaign
We will simulate a targeted employee phishing attack to see how many are cyber aware enough to not fall for it!
Similarly to a vulnerability assessment report, you will receive recommendations on how to improve your human risk posture.
Cyber Security: The Defining Challenge of Our Modern World
of data breaches were caused by human error
reports of cyber security incidents in Australia
of Australians would stop using a product/service from a breached organisation
We are Guaranteed the Security of Our Information
“The success of our company and the service we provide is largely determined by access to information and the security of our systems. For us to provide an efficient service in a secure, digital workplace we needed IT support that is available 24 hours a day, 7 days a week.
With ADITS, we are guaranteed the security of our information always, with this being our top priority as a legal firm. The staff have a fantastic work culture and is comprised of honest people with recognisable values, ensuring excellent, no-nonsense customer service every time.
They are personable by providing a dedicated accounts manager and technical consultant, so I know who I will be speaking to when I call. This further adds to the security of our information and allows us to build trust with the team. I will continue to recommend ADITS to other companies, particularly legal firms, for their service, staff and above all else, security.”

Your Unique Risk Score
We will calculate your overall grade of your company's current cyber risk level.
View Example Report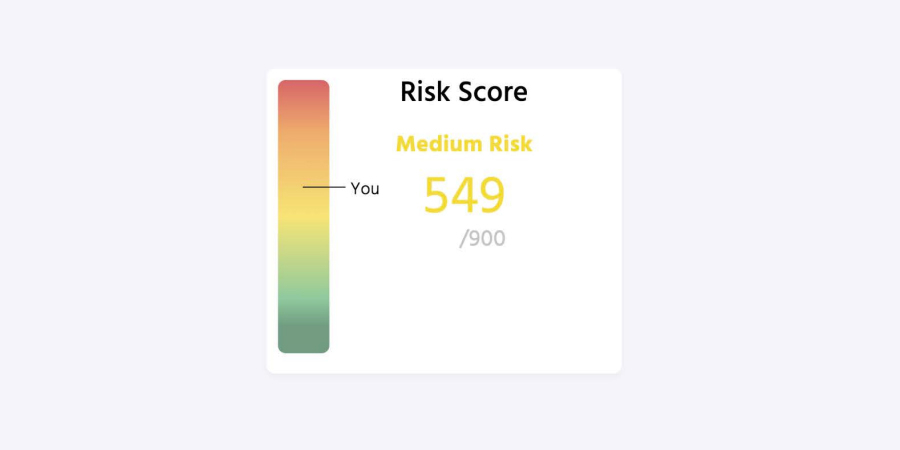
Your Time to Breach
This is an estimated window of time between when an attacker starts looking for a target, to when they have successfully breached your organisation.
View Example Report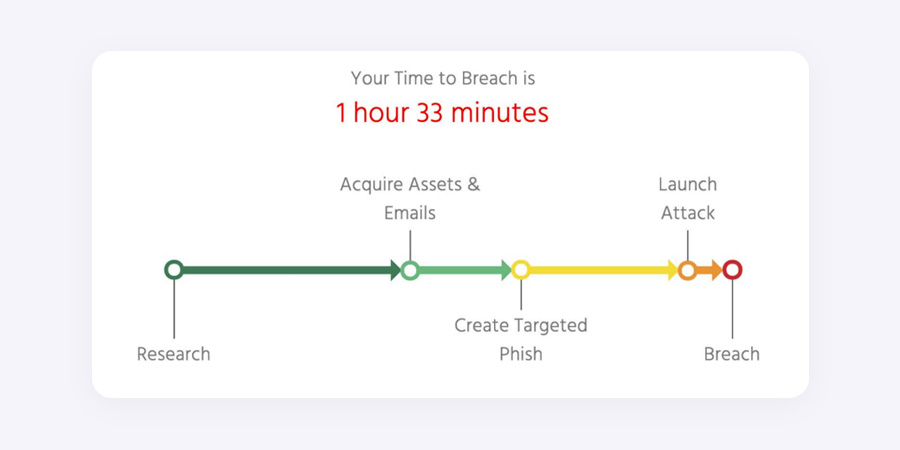
Your Actionable Recommendations
We will analyse all of the different results and provide you with a Human Risk Remediation Programme to reduce the threat of user-related incidents.
View Example Report
The ADITS
Difference
ADITS is known for our outstanding IT solutions and cyber security services.We utilise our expertise, experience, and technology to enable businesses succeed.
Understanding Beyond Business
We understand our clients and take in consideration their unique stories.
Tech Talk, Made Simple
We make sure we translate the tech jargon in plain English.
Embracing Change, Leading Innovation
We lead change in our industry.

Get Started
For a comprehensive and customised analysis of your human risk profile, there’s no better opportunity than our free Human Risk Report. Don't wait until it's too late, start reducing your risk of a data breach today.



