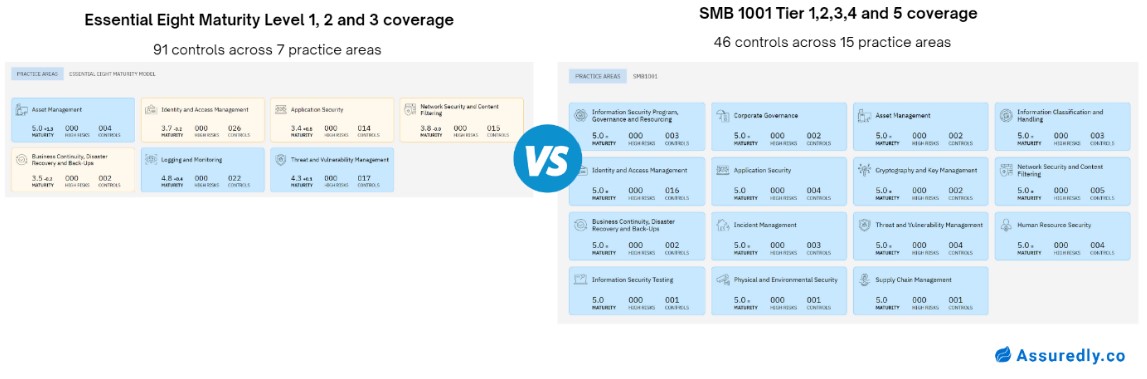
Remembering unique and complex passwords for countless online accounts can feel like an impossible task. Many users try to avoid that by simply using the same password for everything. However, this is a security risk that can lead to a data breach or a cyberattack.
To avert those, password managers are proven as an effective solution. But with different options on the market, what should you consider when choosing a password manager?
1. Make Unmatched Security Your First Priority
Security must always be paramount. Your password safety solution should be a digital fortress, where all your organisation’s credentials are well protected. These specific features can help you sleep soundly at night:
- Encryption: Industry-standard encryption is a must. For instance, the AES-256-bit encryption is military-grade technology that scrambles your data into an unreadable format. That makes it virtually impossible for unauthorised persons to access, even if they breach the system.
- Zero-knowledge architecture: This ensures that only you have access to your passwords. Not even the password manager or your IT manager can see or access your master password or the data stored within your vault.
- Multi-factor authentication (MFA): MFA adds an extra layer of security by requiring a second verification step beyond just your password, such as a code sent to your phone.
2. Simplicity can Give the Best User-Friendly Experience
Complexity often becomes a barrier for most users, so choose a password manager with a user-friendly interface. This will allow everyone in your organisation to easily create, store, and manage their passwords. Look for features like:
- Intuitive interface: A clean, well-designed interface can provide clear navigation and better functionality.
- Cross-platform compatibility: Ensure the password manager works flawlessly across all your team’s devices, from desktops and laptops to mobile phones and tablets.
- Autofill functionality: Automatic login form filling saves time and is more accurate, reducing typographical errors.
3. Powerful Features can Enhance Password Management
Beyond basic password storage, consider additional features that streamline your organisation’s password management. These may include:
- Secure password sharing: Allow authorised staff to securely share access to specific accounts without compromising the master password.
- Password strength reporting: This helps to identify weak passwords within your organisation and encourages strong password creation.
- Data breach monitoring: You can be alerted if any of your organisation’s login details appear on the dark web, which is a red flag for a data breach.
4. Cost-Effectiveness: Balance Security with Your Budget
Password managers offer a range of pricing options. While free versions exist, they often come with limitations in features and user capacity. When choosing a subscription plan, consider these:
- Number of users: Choose a plan that accommodates your current and projected team size.
- Features required: Align your budget with the features you need for optimal password management.
- Scalability: If your organisation is growing, ensure the password manager offers flexible plans to adjust as your needs evolve.
5. Look for Industry Recognition and Customer Trust
Reputation matters. Opt for a password manager with a proven track record of password safety and reliability. Research awards and endorsements from reputable organisations.
Also read customer reviews and testimonials to gain insights into real-world experiences. This can help you decide on a password management app that aligns with your organisation’s needs.
6. Aim for Ease of Deployment and Ongoing Support
Implementing a new system can pose challenges. Choose a password manager with straightforward deployment procedures and readily available support resources. Ask about:
- Clear documentation and training materials: User guides and training resources ensure a smooth transition for your team.
- Dedicated customer support: Access to timely assistance when needed can be invaluable.
7. Test Drive with a Free Trial Before You Commit
Take advantage of free trials to see how the software integrates with your existing workflows and user experience. A hands-on experience can help you determine if the password manager can hack your requirements.
By considering the above tips, you will find the perfect password manager for your business. At ADITS we partner with Keeper, a trusted password management app that ticks all the boxes.
A Better Password Management Experience
Investing in a reliable password manager can greatly reduce the risk of data breaches by protecting your organisation’s sensitive information. It can also bring:
- Increased efficiency, because automating password management saves time and improves productivity
- Improved user experience, as employees appreciate the convenience of a smooth and speedy login process
- Compliance with industry regulations that require sound password management practices, which a password manager can provide
- Cost reduction, by saving on IT costs from reduced password-related support calls and less potential security incidents
Of course, a password manager is not a magic bullet – but it can mean one less thing to worry about for your digital security. A comprehensive cyber security strategy will also include Managed IT, security controls and IT governance.
To safeguard all your organisation’s digital assets, check out our CyberShield and CyberShield + solutions for comprehensive cyber security protection.