The digital revolution has brought not only fantastic opportunities but also increased the attack surface when it comes to threats. Nearly half of Australian SMBs have already been targeted by cyberattacks with the cost of cybercrime averaging between $46,000 to $97,000 for small and medium sized businesses.
These statistics should serve as a wake-up call, highlighting the urgent need for robust cyber protection!
That’s when cyber security frameworks come in. They provide a structured approach to managing cyber risks, ensuring compliance with industry regulations, and incorporating best practices for IT security.
With the many frameworks available these days, this article will delve into the SMB1001 and look at why it is a game changer for smaller organisations.
An Overview of Cyber Security Frameworks
First, it is important to understand that cyber security frameworks provide a common language and methodology for discussing and managing risks. They aim to safeguard your data, systems, and ultimately, your business’ reputation.
Some of the top cyber security frameworks in Australia are ISO 27001, NIST, CIS Controls and the Essential Eight (E8).
The E8 are supported by the Australian Government who developed it through the ACSC back in 2017 to help businesses mitigate cyber threats. While it is not mandatory for private businesses, it is strongly recommended.
After 7 years, we’re able to look back and realise that these traditional frameworks present challenges for smaller organisations that are looking for something less complex, not resource-intensive to implement, and more flexible to suit their needs.
SMB1001: A Clear Path to Cyber Maturity
Cyber Security Certification Australia (CSCAU) developed SMB1001 to fill the gap in cyber security certification for SMBs.
It addresses the unique challenges faced by SMBs in implementing effective cyber security measures without the complexity and high costs associated with larger, more comprehensive frameworks.
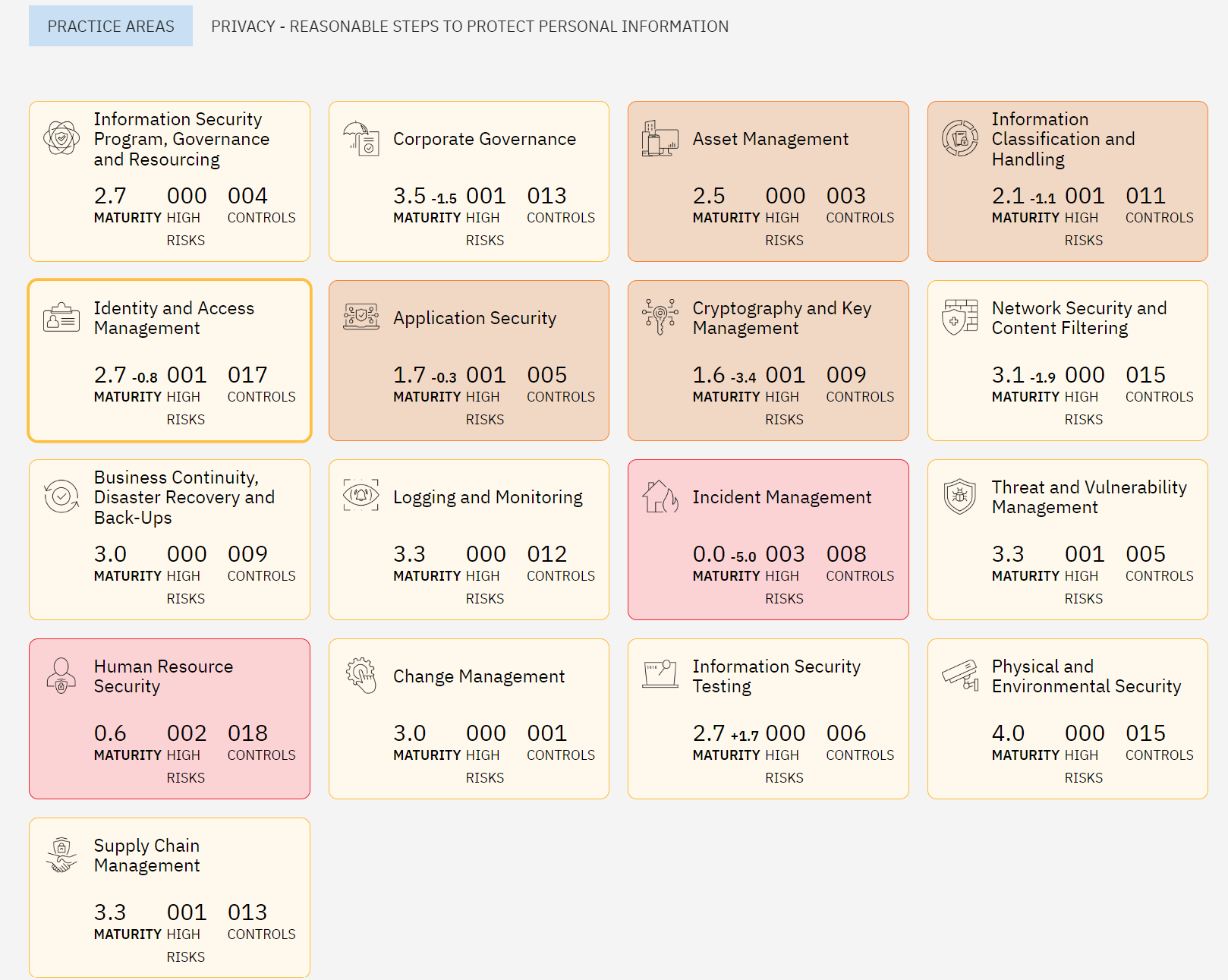
It covers essential security practices across various areas such as incident response, risk management, and employee training, which are often overlooked by simpler frameworks like the Essential Eight.
So, what makes SMB1001 work?
The framework’s certification process is straightforward, practical, and built around five areas of focus:
- Technology Management – This pillar focuses on managing and securing the technology infrastructure, including hardware, software, and networks. It involves implementing security controls such as firewalls, antivirus software, and intrusion detection systems to protect against cyber threats. Regular updates and patch management are also essential to ensure that all systems are protected against known vulnerabilities.
- Access Management – This involves controlling and monitoring access to information systems and data. It includes implementing strong authentication mechanisms, such as multi-factor authentication, to ensure that only authorised individuals have access to sensitive information. Access controls should be regularly reviewed and updated to reflect changes in personnel and roles within the organisation.
- Backup & Recovery – Regular data backups and having a robust recovery plan in place is important. It ensures that data can be restored in the event of a cyber incident, such as a ransomware attack. A well-defined recovery plan helps minimise downtime and ensures business continuity by outlining the steps to be taken to restore systems and data.
- Policies, Plans, & Procedures – this involves developing and implementing comprehensive cybersecurity policies, plans, and procedures. These documents provide guidelines for the organisation’s security practices and response to cyber threats. They should cover areas such as incident response, data protection, and employee responsibilities. Regular reviews and updates are necessary to ensure that the policies remain effective and relevant.
- Education & Training – The SMB1001 framework is designed to be clear, concise, and accessible even for those without a deep technical background. This approach can empower your non-technical staff to take ownership of your cyber security posture. Everybody, at all levels, gets the chance to contribute to keeping the organisation protected. The responsibility of cyber security involves the entire organisation:
- Employees, by following best practices like not opening suspicious emails, using strong passwords, and regularly updating their software.
- Managers, by allocating resources for cyber security training and tools.
- Executives, by prioritising cyber security at a strategic level.
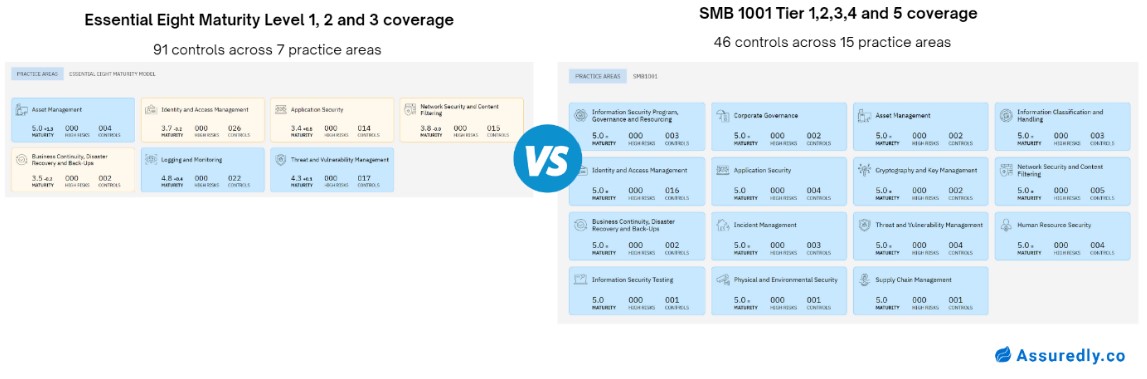
SMB1001 vs. The Essential Eight
Both frameworks have the same goal which is to enhance cyber resilience, but SMB1001 provides a more accessible entry point for businesses of all sizes. It also covers more of the key practice areas that support a robust security program.
In the contrary, the E8 requirements are more technical and complex to comprehend, often leaving small business owners confused and not confident enough to continue building out their security posture.
Take Action with a Reliable Partner
ADITS’ cyber security solution, CyberShield, is built around essential security controls outlined by the SMB1001 :23 Silver Tier 2. Take control of your cyber security today – with expert guidance. ADITS can help your business through comprehensive cyber security services in Brisbane and Townsville.
With data becoming an invaluable asset and stricter rules regarding its protection, we have enhanced our offerings with CyberShield +, an advanced cyber security solution for businesses. It includes everything from CyberShield, plus a cyber security awareness program through uSecure and compliance to the mandatory Privacy Act.